2022祥云杯wp-crypto
little little fermat
题目源码
1 | |
题目分析
根据题目名字来看,此题和费马小定理的使用有关,题目中有一个obfuscate函数,进行了对q的生成,q=p+A,这里可以看一下A的范围,是在2[18,319]之间,因此p、q接近,尝试一下yafu分解。
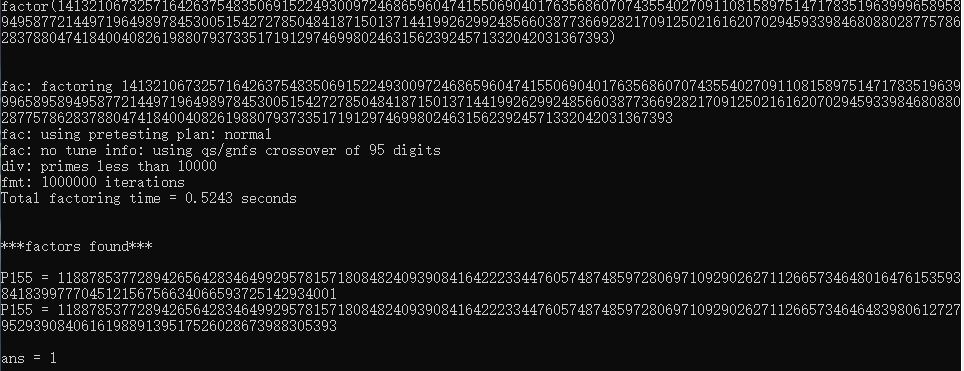 题目对m先进行了处理,再进行RSA加密,因此我们需要知道x。
题目对m先进行了处理,再进行RSA加密,因此我们需要知道x。assert 114514 ** x % p == 1运用费马小定理,若114514与p互素,则x=p-1,即可求解m。
EXP
1 | |
fill
题目源码
1 | |
题目分析
随机产生32位的数,sha256()加密后作为flag,并将其2进制的每一位存到了f_list数组中。
又
创建了一个r_list32位数组,里面存着随机数,先暂时不管。
双
对r_list数组中的随机数做了加密,产生了M数组。
对f_list和M数组进行了numpy.dot运算,即向量乘法,得到和为S。
叒
创建了一个s数组,这个很明显,用LCG线性同余算法进行了加密。
最后将M数组与s数组相加。
这就是这道题整体的流程,每一步并不难,只是步骤多,略显复杂。
EXP
0x01
可以先进行一下LCG的求解,把s数组求解出来,从而求出M数组。
1 | |
0x02
按理来说,感觉应该根据求出来的M数组进行逆运算,求出r_list数组,但是求出来r_list有什么用呢,所以直接尝试求f_list。因为f_list中不是0就是1,与M做向量乘法,即为M数组中若干元素的和。根据题目给定和S,先大概看一下需要M中多少个元素累加。发现在M前21位和
< S,前22位和 >
S,所以猜想应该是M当中,除10个左右元素之外的和。
这里就遍历了一下,复杂度实在太高了,也没想着能出,结果还真算出来了o.O
1 | |
也就说明,f_list中下标为这些的,对应值是0,其余为1,即可得到msg的2进制数,转为十进制后进行sha256()加密即可。
1 | |
2022祥云杯wp-crypto
https://sch01ar.github.io/2022/10/30/2022-10-30-2022祥云杯wp-crypto/